QUESTION 271
Your network contains an Active Directory domain named adatum.com. You create a new Group Policy object (GPO) named GPO1.
You need to verify that GPO1 was replicated to all of the domain controllers.
Which tool should you use?
A. Gpupdate
B. Gpresult
C. Group Policy Management
D. Active Directory Sites and Services
Answer: C
QUESTION 272
Your network contains two Web servers named Server1 and Server2. Both servers run Windows Server 2012 R2.
Server1 and Server2 are nodes in a Network Load Balancing (NLB) cluster. The NLB cluster contains an application named App1 that is accessed by using the URL http://app1.contoso.com.
You plan to perform maintenance on Server1.
You need to ensure that all new connections to App1 are directed to Server2. The solution must not disconnect the existing connections to Server1.
What should you run?
A. The Set-NlbCluster cmdlet
B. The Set-NlbClusterNode cmdlet
C. The Stop-NlbCluster cmdlet
D. The Stop-NlbClusterNode cmdlet
Answer: D
Explanation:
The Stop-NlbClusterNode cmdlet stops a node in an NLB cluster. When you use the stop the nodes in the cluster, client connections that are already in progress are interrupted. To avoid interrupting active connections, consider using the -drain parameter, which allows the node to continue servicing active connections but disables all new traffic to that node.
-Drain <SwitchParameter>
Drains existing traffic before stopping the cluster node. If this parameter is omitted, existing traffic will be dropped.
QUESTION 273
Hotspot Question
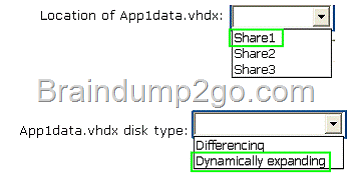
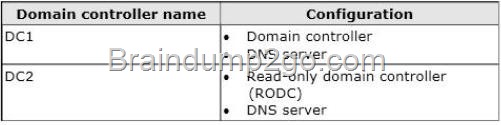
Your network contains an Active Directory domain named contoso.com.
You have a failover cluster named Cluster1 that contains two nodes named Server1 and Server2. Both servers run Windows Server 2012 R2 and have the Hyper-V server role installed.
You plan to create two virtual machines that will run an application named App1. App1 will store data on a virtual hard drive named App1data.vhdx. App1data.vhdx will be shared by both virtual machines.
The network contains the following shared folders:
– An SMB file share named Share1 that is hosted on a Scale-Out File Server.
– An SMB file share named Share2 that is hosted on a standalone file server.
– An NFS share named Share3 that is hosted on a standalone file server.
You need to ensure that both virtual machines can use App1data.vhdx simultaneously.
What should you do?
To answer, select the appropriate configurations in the answer area.
![clip_image001[8] clip_image001[8]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A7C2/clip_image0018_thumb.jpg)
![clip_image001[10] clip_image001[10]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A7C2/clip_image00110_thumb.jpg)
Answer:
QUESTION 274
Your network contains an Active directory forest named contoso.com. The forest contains two child domains named east.contoso.com and west.contoso.com.
You install an Active Directory Rights Management Services (AD RMS) cluster in each child domain.
You discover that all of the users in the contoso.com forest are directed to the AD RMS cluster in east.contoso.com.
You need to ensure that the users in west.contoso.com are directed to the AD RMS cluster in west.contoso.com and that the users in east.contoso.com are directed to the AD RMS cluster in east.contoso.com.
What should you do?
A. Modify the Service Connection Point (SCP).
B. Configure the Group Policy object (GPO) settings of the users in the west.contoso.com domain.
C. Configure the Group Policy object (GPO) settings of the users in the east.contoso.com domain.
D. Modify the properties of the AD RMS cluster in west.contoso.com.
Answer: C
QUESTION 275
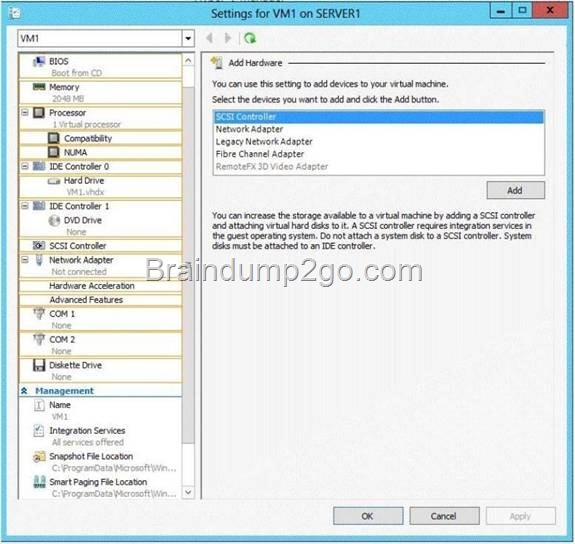
You have a server named Server1 that runs Windows Server 2012 R2.
From Server Manager, you install the Active Directory Certificate Services server role on Server1.
A domain administrator named Admin1 logs on to Server1.
When Admin1 runs the Certification Authority console, Admin1 receive the following error message.
![clip_image001[12] clip_image001[12]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A7C2/clip_image00112_thumb.jpg)
You need to ensure that when Admin1 opens the Certification Authority console on Server1, the error message does not appear.
What should you do?
A. Install the Active Directory Certificate Services (AD CS) tools.
B. Run the regsvr32.exe command.
C. Modify the PATH system variable.
D. Configure the Active Directory Certificate Services server role from Server Manager.
Answer: D
QUESTION 276
Your network contains an Active Directory domain named contoso.com. The domain contains a member server named Server1 that has the Active Directory Federation Services server role installed. All servers run Windows Server 2012.d
You complete the Active Directory Federation Services Configuration Wizard on Server1.
You need to ensure that client devices on the internal network can use Workplace Join.
Which two actions should you perform on Server1? (Each correct answer presents part of the solution. Choose two.)
A. Run Enable-AdfsDeviceRegistration -PrepareActiveDirectory.
B. Edit the multi-factor authentication global authentication policy settings.
C. Run Enable-AdfsDeviceRegistration.
D. Run Set-AdfsProxyProperties HttpPort 80.
E. Edit the primary authentication global authentication policy settings.
Answer: CE
Explanation:
* To enable Device Registration Service On your federation server, open a Windows PowerShell command window and type:
Enable-AdfsDeviceRegistration
Repeat this step on each federation farm node in your AD FS farm..
Enable seamless second factor authentication
Seamless second factor authentication is an enhancement in AD FS that provides an added level of access protection to corporate resources and applications from external devices that are trying to access them. When a personal device is Workplace Joined, it becomes a `known’ device and administrators can use this information to drive conditional access and gate access to resources.
To enable seamless second factor authentication, persistent single sign-on (SSO) and conditional access for Workplace Joined devices
In the AD FS Management console, navigate to Authentication Policies. Select Edit Global Primary Authentication. Select the check box next to Enable Device Authentication, and then click OK.
QUESTION 277
Drag and Drop Question
Your network contains an Active Directory domain named contoso.com.
You need to ensure that third-party devices can use Workplace Join to access domain resources on the Internet.
Which four actions should you perform in sequence?
To answer, move the appropriate four actions from the list of actions to the answer area and arrange them in the correct order.
![clip_image002[5] clip_image002[5]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A7C2/clip_image0025_thumb.jpg)
Answer:
![clip_image002[7] clip_image002[7]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A7C2/clip_image0027_thumb.jpg)
QUESTION 278
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2 and has the DHCP Server server role installed.
You need to create an IPv6 scope on Server1. The scope must use an address space that is reserved for private networks. The addresses must be routable.
Which IPV6 scope prefix should you use?
A. 2001:123:4567:890A::
B. FE80:123:4567::
C. FF00:123:4567:890A::
D. FD00:123:4567::
Answer: D
QUESTION 279
Hotspot Question
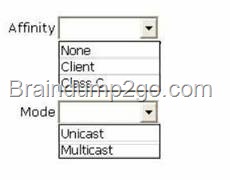
Your network contains an Active Directory domain named contoso.com. The domain contains two servers named Server1 and Server2. All servers run Windows Server 2012 R2.
You install the DHCP Server server role on both servers.
On Server1, you have the DHCP scope configured as shown in the exhibit. (Click the Exhibit button.)
![clip_image001[14] clip_image001[14]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A7C2/clip_image00114_thumb.jpg)
You need to configure the scope to be load-balanced across Server1 and Server2.
What Windows PowerShell cmdlet should you run on Server1?
To answer, select the appropriate options in the answer area.
![clip_image002[9] clip_image002[9]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A7C2/clip_image0029_thumb.jpg)
Answer:
![clip_image002[11] clip_image002[11]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A7C2/clip_image00211_thumb.jpg)
QUESTION 280
Hotspot Question
Your network contains an Active Directory domain named contoso.com. The domain contains two DHCP servers named Server1 and Server2. Both servers have multiple IPv4 scopes.
Server1 and Server2 are used to assign IP addresses for the network IDs of 172.20.0.0/16 and 131.107.0.0/16.
You install the IP Address Management (IPAM) Server feature on a server named IPAM1 and configure IPAM1 to manage Server1 and Server2.
Some users from the 172.20.0.0 network report that they occasionally receive an IP address conflict error message.
You need to identify whether any scopes in the 172.20.0.0 network ID conflict with one another.
What Windows PowerShell cmdlet should you run?
To answer, select the appropriate options in the answer area.
![clip_image002[13] clip_image002[13]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A7C2/clip_image00213_thumb.jpg)
Answer:
![clip_image002[15] clip_image002[15]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A7C2/clip_image00215_thumb.jpg)
Passing Microsoft 70-412 Exam successfully in a short time! Just using Braindump2go’s Latest Microsoft 70-412 Dump: http://www.braindump2go.com/70-412.html
![clip_image002[1] clip_image002[1]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A7C2/clip_image0021_thumb.jpg)
![clip_image002[3] clip_image002[3]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A7C2/clip_image0023_thumb.jpg)
![clip_image001[4] clip_image001[4]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A7C2/clip_image0014_thumb.jpg)
![clip_image001[6] clip_image001[6]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A7C2/clip_image0016_thumb.jpg)
![clip_image001[1] clip_image001[1]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_9B0A/clip_image0011_thumb.jpg)
![clip_image001[4] clip_image001[4]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_9B0A/clip_image0014_thumb_3.jpg)
![clip_image001[6] clip_image001[6]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_9B0A/clip_image0016_thumb_3.jpg)
![clip_image001[8] clip_image001[8]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_9B0A/clip_image0018_thumb_3.jpg)
![clip_image001[10] clip_image001[10]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_9B0A/clip_image00110_thumb_3.jpg)
![clip_image001[12] clip_image001[12]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_9B0A/clip_image00112_thumb_3.jpg)
![clip_image002[12] clip_image002[12]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_9B0A/clip_image00212_thumb.jpg)
![clip_image002[14] clip_image002[14]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_9B0A/clip_image00214_thumb.jpg)
![clip_image002[16] clip_image002[16]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_9B0A/clip_image00216_thumb.jpg)
![clip_image001[30] clip_image001[30]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_9B0A/clip_image00130_thumb.jpg)
![clip_image001[32] clip_image001[32]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_9B0A/clip_image00132_thumb.jpg)
![clip_image001[18] clip_image001[18]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_9B0A/clip_image00118_thumb.jpg)
![clip_image001[20] clip_image001[20]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_9B0A/clip_image00120_thumb.jpg)
![clip_image001[22] clip_image001[22]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_9B0A/clip_image00122_thumb.jpg)
![clip_image002[6] clip_image002[6]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_9B0A/clip_image0026_thumb.jpg)
![clip_image002[8] clip_image002[8]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_9B0A/clip_image0028_thumb.jpg)
![clip_image002[10] clip_image002[10]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_9B0A/clip_image00210_thumb.jpg)
![clip_image001[24] clip_image001[24]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_9B0A/clip_image00124_thumb.jpg)
![clip_image001[26] clip_image001[26]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_9B0A/clip_image00126_thumb.jpg)
![clip_image001[28] clip_image001[28]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_9B0A/clip_image00128_thumb.jpg)
![clip_image001[4] clip_image001[4]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_9B0A/clip_image0014_thumb.jpg)
![clip_image001[6] clip_image001[6]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_9B0A/clip_image0016_thumb.jpg)
![clip_image001[8] clip_image001[8]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_9B0A/clip_image0018_thumb.jpg)
![clip_image002[4] clip_image002[4]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_9B0A/clip_image0024_thumb.jpg)
![clip_image001[10] clip_image001[10]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_9B0A/clip_image00110_thumb.jpg)
![clip_image001[12] clip_image001[12]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_9B0A/clip_image00112_thumb.jpg)
![clip_image001[14] clip_image001[14]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_9B0A/clip_image00114_thumb.jpg)
![clip_image001[16] clip_image001[16]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_9B0A/clip_image00116_thumb.jpg)
![clip_image001[52] clip_image001[52]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00152_thumb.jpg)
![clip_image001[54] clip_image001[54]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00154_thumb.jpg)
![clip_image001[56] clip_image001[56]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00156_thumb.jpg)
![clip_image002[64] clip_image002[64]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00264_thumb.jpg)
![clip_image001[58] clip_image001[58]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00158_thumb.jpg)
![clip_image001[60] clip_image001[60]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00160_thumb.jpg)
![clip_image002[44] clip_image002[44]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00244_thumb.jpg)
![clip_image002[46] clip_image002[46]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00246_thumb.jpg)
![clip_image001[36] clip_image001[36]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00136_thumb.jpg)
![clip_image002[48] clip_image002[48]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00248_thumb.jpg)
![clip_image002[50] clip_image002[50]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00250_thumb.jpg)
![clip_image002[52] clip_image002[52]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00252_thumb.jpg)
![clip_image002[54] clip_image002[54]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00254_thumb.jpg)
![clip_image001[38] clip_image001[38]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00138_thumb.jpg)
![clip_image001[40] clip_image001[40]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00140_thumb.jpg)
![clip_image002[56] clip_image002[56]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00256_thumb.jpg)
![clip_image001[42] clip_image001[42]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00142_thumb.jpg)
![clip_image002[58] clip_image002[58]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00258_thumb.jpg)
![clip_image001[44] clip_image001[44]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00144_thumb.jpg)
![clip_image002[60] clip_image002[60]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00260_thumb.jpg)
![clip_image002[62] clip_image002[62]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00262_thumb.jpg)
![clip_image001[46] clip_image001[46]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00146_thumb.jpg)
![clip_image001[48] clip_image001[48]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00148_thumb.jpg)
![clip_image001[50] clip_image001[50]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00150_thumb.jpg)
![clip_image002[4] clip_image002[4]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image0024_thumb.jpg)
![clip_image002[8] clip_image002[8]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image0028_thumb.jpg)
![clip_image002[10] clip_image002[10]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00210_thumb.jpg)
![clip_image002[12] clip_image002[12]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00212_thumb.jpg)
![clip_image002[14] clip_image002[14]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00214_thumb.jpg)
![clip_image002[16] clip_image002[16]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00216_thumb.jpg)
![clip_image002[18] clip_image002[18]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00218_thumb.jpg)
![clip_image001[34] clip_image001[34]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00134_thumb.jpg)
![clip_image002[20] clip_image002[20]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00220_thumb.jpg)
![clip_image002[22] clip_image002[22]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00222_thumb.jpg)
![clip_image002[24] clip_image002[24]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00224_thumb.jpg)
![clip_image002[26] clip_image002[26]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00226_thumb.jpg)
![clip_image002[28] clip_image002[28]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00228_thumb.jpg)
![clip_image002[30] clip_image002[30]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00230_thumb.jpg)
![clip_image002[32] clip_image002[32]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00232_thumb.jpg)
![clip_image002[34] clip_image002[34]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00234_thumb.jpg)
![clip_image002[36] clip_image002[36]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00236_thumb.jpg)
![clip_image002[38] clip_image002[38]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00238_thumb.jpg)
![clip_image002[40] clip_image002[40]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00240_thumb.jpg)
![clip_image002[42] clip_image002[42]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00242_thumb.jpg)
![clip_image001[18] clip_image001[18]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00118_thumb.jpg)
![clip_image001[20] clip_image001[20]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00120_thumb.jpg)
![clip_image001[22] clip_image001[22]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00122_thumb.jpg)
![clip_image001[24] clip_image001[24]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00124_thumb.jpg)
![clip_image001[26] clip_image001[26]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00126_thumb.jpg)
![clip_image001[28] clip_image001[28]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00128_thumb.jpg)
![clip_image001[30] clip_image001[30]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00130_thumb.jpg)
![clip_image001[32] clip_image001[32]](http://examgod.com/l2pimages/Official-2014-Latest-Microsoft-70-412-Ex_A25E/clip_image00132_thumb.jpg)