QUESTION 281
Your network contains an Active Directory forest named contoso.com. The forest contains a single domain. All servers runs Windows Server 2012 R2.The domain contains two domain controllers named DC1 and DC2. Both domain controllers are virtual machines on a HyperV host. You plan to create a cloned domain controller named DC3 from an image of DC1. You need to ensure that you can clone DC1. Which two actions should you perform? (Each correct answer presents part of the solution.
Choose two.)
A. Add the computer account of DC1 to the Cloneable Domain Controllers group.
B. Create a DCCIoneConfig.xml file on DC1.
C. Add the computer account of DC3 to the Cloneable Domain Controllers group.
D. Run the Enable-AdOptionalFeaturecmdlet.
E. Modify the contents of the DefaultDCCIoneAllowList.xml file on DC1.
Answer: AB
Explanation:
A: Cloneable Domain Controllers Group There’s a new group in town. It’s called Cloneable Domain Controllers and you can find it in the Users container. Membership in this group dictates whether a DC can or cannot be cloned. This group has some permissions set on the domain head that should not be removed. Removing these permissions will cause cloning to fail. Also, as a best practice, DCs shouldn’t be added to the group until you plan to clone and DCs should be removed from the group once cloning is complete. Cloned DCs will also end up in the Cloneable Domain Controllers group.
B: DCCloneConfig.xml
There’s one key difference between a cloned DC and a DC that is being restored to a previous snapshot: DCCloneConfig.XML.
DCCloneConfig.xml is an XML configuration file that contains all of the settings the cloned DC will take when it boots. This includes network settings, DNS, WINS, AD site name, new DC name and more. This file can be generated in a few different ways.
The New-ADDCCloneConfigcmdlet in PowerShell
By hand with an XML editor
By editing an existing config file, again with an XML editor. Reference: Virtual Domain Controller Cloning in Windows Server 2012
QUESTION 282
Your network contains an Active Directory forest. The forest contains two domains named contoso.com and corp.contoso.com. All domain controllers run Windows Server 2012 R2 and are configured as global catalog servers. The corp.contoso.com domain contains a domain controller named DC1. You need to disable the global catalog on DC1. What should you do?
A. From Active Directory Users and Computers, modify the properties of the DC1 computer account.
B. From Active Directory Administrative Center, modify the properties of the DC1 computer account.
C. From Active Directory Sites and Services, modify the NTDS Settings of the DC1 server object.
D. From Active Directory Domains and Trusts, modify the properties of the corp.contoso.com domain.
Answer: C
Explanation:
http://technet.microsoft.com/en-us/library/cc755257.aspx
To add or remove the global catalog
Open Active Directory Sites and Services. To open Active Directory Sites and Services, click Start , click Administrative Tools , and then click Active Directory Sites and Services .
To open Active Directory Sites and Services in Windows Server® 2012, click Start , type dssite.msc .
In the console tree, click the server object to which you want to add the global catalog or from which you want to remove the global catalog.
Where?
Active Directory Sites and Services\Sites\SiteName\Servers
In the details pane, right-click NTDS Settings of the selected server object, and then click Properties .
Select the Global Catalog check box to add the global catalog, or clear the check box to remove the global catalog.
QUESTION 283
Your network contains an Active Directory domain named contoso.com. Your company hires 500 temporary employees for the summer. The human resources department gives you a Microsoft Excel document that contains a list of the temporary employees. You need to automate the creation of user accounts for the 500 temporary employees. Which tool or tools should you use?
A. The Set-ADUsercmdlet and the Add-Member cmdlet
B. The Import-CSV cmdlet and the New-ADUsercmdlet
C. ADSI Edit
D. Active Directory Users and Computers
Answer: B
Explanation:
http://technet.microsoft.com/en-us/library/ee176874.aspx
The CSVDE is a command-line utility that can create new AD DS objects by importing information from a comma-separated value (.csv) file. This would be the least amount of administrative effort in this case especially considering that these would be temporary employees.
QUESTION 284
Hotspot Question
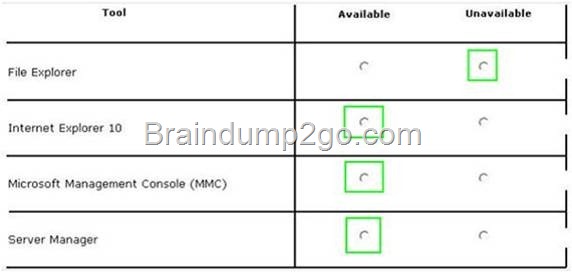
You deploy a Server with a GUI installation of Windows Server 2012 R2 Datacenter. From Windows PowerShell, you run the following command: Remove-WindowsFeature ServerGui-Shell. In the table below, identify which tools are available on Server1 and which tools are unavailable on Server1. Make only one selection in each row. Each correct selection is worth one point.
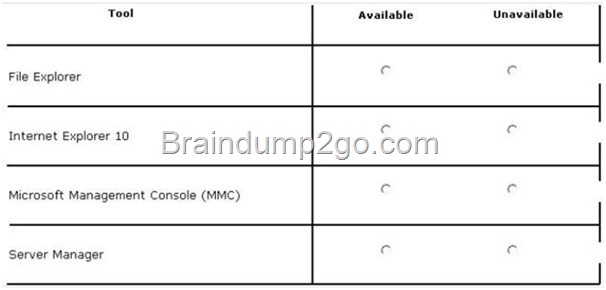
Answer:
QUESTION 285
Drag and Drop Question
Your network contains an Active Directory domain named contoso.com. The domain contains two servers named Server1 and Server2. Server1 and Server2 run a Server with a GUI installation of Windows Server 2012 R2. You remove the Graphical Management Tools and Infrastructure feature on Server2. You need to restart Server2. What should you do? (To answer, drag the appropriate tools to the correct statements. Each tool may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)
![clip_image001[4] clip_image001[4]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image0014_thumb.jpg)
Answer:
![clip_image002[4] clip_image002[4]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image0024_thumb.jpg)
QUESTION 286
Drag and Drop Question
You have a server that runs Windows Server 2012 R2. You need to create a volume that will remain online if two disks in the volume fail. The solution must minimize the number of disks used to create the volume. Which three actions should you perform in sequence? (To answer, move the appropriate three actions from the list of actions to the answer area and arrange them in the correct order.)
![clip_image001[6] clip_image001[6]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image0016_thumb.jpg)
Answer:
QUESTION 287
Hotspot Question
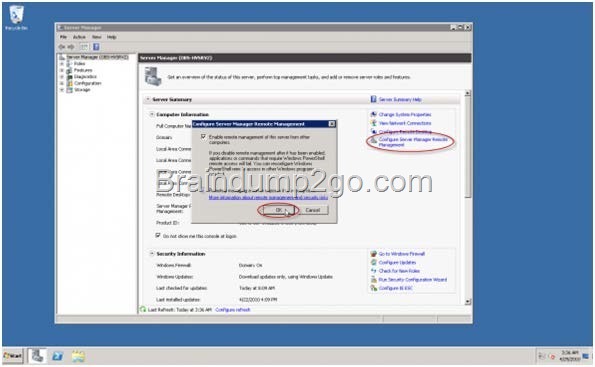
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server that runs Windows Server 2012 R2. You perform a Server Core Installation of Windows Server 2012 R2 on a new server. You need to ensure that you can add the new server to Server Manager on Server1. What should you configure on the new server?To answer, select the appropriate setting in the answer area.
QUESTION 288
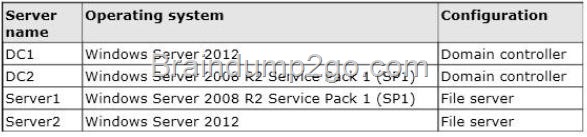
You work as an administrator at L2P.com. The L2P.com network consists of a single domain named L2P.com. All servers in the L2P.com domain, including domain controllers, have Windows Server 2012 installed.
You have been instructed to modify the name of the local Administrator account on all L2P.com workstations. You want to achieve this using as little administrative effort as possible.
Which of the following actions should you take?
You should consider configuring the Security Options settings via the Group Policy
A. You should consider configuring the Security Options settings via the Group Policy Management
Console (GPMC).
B. You should consider navigating to Local Users and Groups via Computer
C. You should consider configuring the replication settings.
D. You should consider navigating to Local Users and Groups via Computer Management on each workstation.
Answer: A
Explanation:
Rename administrator account policy setting determines whether a different account name is associated with the security identifier (SID) for the Administrator account.
Because the Administrator account exists on all Windows server versions, renaming the account makes it slightly more difficult for attackers to guess this user name and password combination. By default, the built-in Administrator account cannot be locked out no matter how many times a malicious user might use a bad password. This makes the Administrator account a popular target for brute-force password-guessing attacks. The value of this countermeasure is lessened because this account has a well-known SID and there are non-Microsoft tools that allow you to initiate a brute-force attack over the network by specifying the SID rather than the account name. This means that even if you have renamed the Administrator account, a malicious user could start a brute-force attack by using the SID.
Rename the Administrator account by specifying a value for the Accounts: Rename administrator account policy setting.
Location: GPO_name\Computer Configuration\Windows Settings\Security Settings\Local
Policies\Security Options
http://technet.microsoft.com/en-us/library/jj852273%28v=ws.10%29.aspx http://windowsitpro.com/group-policy/securing-administrator-account
QUESTION 289
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1. Server1 runs Windows Server 2012 R2. An administrator creates a security template named Template1. You need to App1y Template1 to Server1. Which snap-in should you use?
A. Security Templates
B. Authorization Manager
C. Security Configuration and Analysis
D. Resultant Set of Policy
Answer: C
QUESTION 290
Your network contains an Active Directory forest named contoso.com. The forest contains a single domain. The domain contains two domain controllers named DC1 and DC2 that run Windows Server 2012 R2. The domain contains a user named User1 and three global security groups named Group1, Group2 and, Group3. You need to add User1 to Group1, Group2, and Group3. Which cmdlet should you run?
A. Add-AdPrincipalGroupMembership
B. Install- AddsDomainController
C. Install- WindowsFeature
D. Install-AddsDomain
E. Rename-AdObject
F. Set-AdAccountControl
G. Set-AdGroup
H. Set-User
Answer: A
Explanation:
http://technet.microsoft.com/en-us/library/ee617203.aspx
The Add-ADPrincipalGroupMembership cmdlet adds a user, group, service account, or computer as a new member to one or more Active Directory groups.
Passing Microsoft 70-410 Exam successfully in a short time! Just using Braindump2go’s Latest Microsoft 70-410 Dump:
![clip_image002[6] clip_image002[6]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image0026_thumb.jpg)
![clip_image001[8] clip_image001[8]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image0018_thumb.jpg)
![clip_image002[8] clip_image002[8]](http://examgod.com/l2pimages/5bae3a6b6b06_76F1/clip_image0028_thumb_3.jpg)
![clip_image001[65] clip_image001[65]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00165_thumb.jpg)
![clip_image001[67] clip_image001[67]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00167_thumb.jpg)
![clip_image001[69] clip_image001[69]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00169_thumb.jpg)
![clip_image001[71] clip_image001[71]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00171_thumb.jpg)
![clip_image001[73] clip_image001[73]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00173_thumb.jpg)
![clip_image002[38] clip_image002[38]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00238_thumb.jpg)
![clip_image002[40] clip_image002[40]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00240_thumb.jpg)
![clip_image002[42] clip_image002[42]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00242_thumb.jpg)
![clip_image002[44] clip_image002[44]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00244_thumb.jpg)
![clip_image001[75] clip_image001[75]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00175_thumb.jpg)
![clip_image002[46] clip_image002[46]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00246_thumb.jpg)
![clip_image002[48] clip_image002[48]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00248_thumb.jpg)
![clip_image002[50] clip_image002[50]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00250_thumb.jpg)
![clip_image002[52] clip_image002[52]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00252_thumb.jpg)
![clip_image001[77] clip_image001[77]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00177_thumb.jpg)
![clip_image001[79] clip_image001[79]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00179_thumb.jpg)
![clip_image001[55] clip_image001[55]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00155_thumb.jpg)
![clip_image001[57] clip_image001[57]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00157_thumb.jpg)
![clip_image002[30] clip_image002[30]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00230_thumb.jpg)
![clip_image002[32] clip_image002[32]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00232_thumb.jpg)
![clip_image001[59] clip_image001[59]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00159_thumb.jpg)
![clip_image002[36] clip_image002[36]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00236_thumb.jpg)
![clip_image001[61] clip_image001[61]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00161_thumb.jpg)
![clip_image001[63] clip_image001[63]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00163_thumb.jpg)
![clip_image001[33] clip_image001[33]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00133_thumb.jpg)
![clip_image002[18] clip_image002[18]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00218_thumb.jpg)
![clip_image001[35] clip_image001[35]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00135_thumb.jpg)
![clip_image001[37] clip_image001[37]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00137_thumb.jpg)
![clip_image001[39] clip_image001[39]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00139_thumb.jpg)
![clip_image001[41] clip_image001[41]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00141_thumb.jpg)
![clip_image002[20] clip_image002[20]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00220_thumb.jpg)
![clip_image002[22] clip_image002[22]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00222_thumb.jpg)
![clip_image002[24] clip_image002[24]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00224_thumb.jpg)
![clip_image002[26] clip_image002[26]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00226_thumb.jpg)
![clip_image002[28] clip_image002[28]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00228_thumb.jpg)
![clip_image001[43] clip_image001[43]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00143_thumb.jpg)
![clip_image001[45] clip_image001[45]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00145_thumb.jpg)
![clip_image001[47] clip_image001[47]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00147_thumb.jpg)
![clip_image001[49] clip_image001[49]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00149_thumb.jpg)
![clip_image001[51] clip_image001[51]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00151_thumb.jpg)
![clip_image001[53] clip_image001[53]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00153_thumb.jpg)
![clip_image001[25] clip_image001[25]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00125_thumb.jpg)
![clip_image002[12] clip_image002[12]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00212_thumb.jpg)
![clip_image001[27] clip_image001[27]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00127_thumb.jpg)
![clip_image001[29] clip_image001[29]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00129_thumb.jpg)
![clip_image002[14] clip_image002[14]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00214_thumb.jpg)
![clip_image001[31] clip_image001[31]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00131_thumb.jpg)
![clip_image002[16] clip_image002[16]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00216_thumb.jpg)
![clip_image001[12] clip_image001[12]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00112_thumb.jpg)
![clip_image001[14] clip_image001[14]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00114_thumb.jpg)
![clip_image002[6] clip_image002[6]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image0026_thumb.jpg)
![clip_image001[16] clip_image001[16]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00116_thumb.jpg)
![clip_image001[18] clip_image001[18]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00118_thumb.jpg)
![clip_image001[21] clip_image001[21]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00121_thumb.jpg)
![clip_image001[23] clip_image001[23]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00123_thumb.jpg)
![clip_image002[8] clip_image002[8]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image0028_thumb.jpg)
![clip_image002[10] clip_image002[10]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00210_thumb.jpg)
![clip_image001[4] clip_image001[4]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image0014_thumb.jpg)
![clip_image001[6] clip_image001[6]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image0016_thumb.jpg)
![clip_image001[8] clip_image001[8]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image0018_thumb.jpg)
![clip_image001[10] clip_image001[10]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00110_thumb.jpg)
![clip_image002[4] clip_image002[4]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image0024_thumb.jpg)
![clip_image001[4] clip_image001[4]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0014_thumb_4.jpg)
![clip_image001[6] clip_image001[6]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0016_thumb_4.jpg)
![clip_image001[8] clip_image001[8]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0018_thumb_4.jpg)
![clip_image001[10] clip_image001[10]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00110_thumb_4.jpg)
![clip_image001[12] clip_image001[12]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00112_thumb_4.jpg)
![clip_image001[14] clip_image001[14]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00114_thumb_3.jpg)
![clip_image001[16] clip_image001[16]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00116_thumb_3.jpg)
![clip_image001[18] clip_image001[18]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00118_thumb_3.jpg)
![clip_image001[20] clip_image001[20]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00120_thumb_3.jpg)
![clip_image002[4] clip_image002[4]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0024_thumb_4.jpg)
![clip_image001[22] clip_image001[22]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00122_thumb_3.jpg)

![clip_image001[4] clip_image001[4]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0014_thumb_3.jpg)
![clip_image001[6] clip_image001[6]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0016_thumb_3.jpg)
![clip_image001[8] clip_image001[8]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0018_thumb_3.jpg)
![clip_image001[10] clip_image001[10]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00110_thumb_3.jpg)
![clip_image001[12] clip_image001[12]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00112_thumb_3.jpg)
![clip_image002[4] clip_image002[4]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0024_thumb_3.jpg)
![clip_image002[6] clip_image002[6]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0026_thumb_3.jpg)
![clip_image002[8] clip_image002[8]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0028_thumb_3.jpg)
![clip_image001[30] clip_image001[30]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00130_thumb.jpg)
![clip_image001[32] clip_image001[32]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00132_thumb.jpg)
![clip_image002[28] clip_image002[28]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00228_thumb.jpg)
![clip_image002[30] clip_image002[30]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00230_thumb.jpg)
![clip_image002[32] clip_image002[32]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00232_thumb.jpg)
![clip_image002[34] clip_image002[34]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00234_thumb.jpg)
![clip_image001[34] clip_image001[34]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00134_thumb.jpg)
![clip_image001[36] clip_image001[36]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00136_thumb.jpg)
![clip_image002[36] clip_image002[36]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00236_thumb.jpg)
![clip_image002[38] clip_image002[38]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00238_thumb.jpg)
![clip_image001[38] clip_image001[38]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00138_thumb.jpg)
![clip_image001[40] clip_image001[40]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00140_thumb.jpg)
![clip_image001[42] clip_image001[42]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00142_thumb.jpg)
![clip_image001[44] clip_image001[44]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00144_thumb.jpg)
![clip_image002[40] clip_image002[40]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00240_thumb.jpg)
![clip_image001[46] clip_image001[46]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00146_thumb.jpg)
![clip_image001[18] clip_image001[18]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00118_thumb.jpg)
![clip_image001[20] clip_image001[20]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00120_thumb.jpg)
![clip_image002[20] clip_image002[20]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00220_thumb.jpg)
![clip_image002[22] clip_image002[22]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00222_thumb.jpg)
![clip_image002[24] clip_image002[24]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00224_thumb.jpg)
![clip_image002[26] clip_image002[26]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00226_thumb.jpg)
![clip_image001[22] clip_image001[22]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00122_thumb.jpg)
![clip_image001[24] clip_image001[24]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00124_thumb.jpg)
![clip_image001[26] clip_image001[26]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00126_thumb.jpg)
![clip_image001[28] clip_image001[28]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00128_thumb.jpg)
![clip_image002[4] clip_image002[4]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0024_thumb.jpg)
![clip_image002[6] clip_image002[6]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0026_thumb.jpg)
![clip_image002[8] clip_image002[8]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0028_thumb.jpg)
![clip_image002[10] clip_image002[10]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00210_thumb.jpg)
![clip_image002[12] clip_image002[12]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00212_thumb.jpg)
![clip_image001[4] clip_image001[4]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0014_thumb.jpg)
![clip_image001[6] clip_image001[6]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0016_thumb.jpg)
![clip_image002[14] clip_image002[14]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00214_thumb.jpg)
![clip_image002[16] clip_image002[16]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00216_thumb.jpg)
![clip_image001[8] clip_image001[8]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0018_thumb.jpg)
![clip_image001[10] clip_image001[10]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00110_thumb.jpg)
![clip_image001[12] clip_image001[12]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00112_thumb.jpg)
![clip_image001[14] clip_image001[14]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00114_thumb.jpg)
![clip_image001[16] clip_image001[16]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00116_thumb.jpg)
![clip_image002[18] clip_image002[18]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00218_thumb.jpg)