JUNIPER OFFICIAL NEWS: JN0-633 Exam Questions have been Updated Today! Get the Latest JN0-633 Dumps Full Version from Braindump2go Now!
100% Pass JN0-633 Real Test is not a dream! Braindump2go Latest Released JN0-633 Exam Practice Exam Dumps will help you pass JN0-633 Exam one time easiluy! Free Sample Exam Questions and Answers are offered for free download now! Quickly having a try today! Never loose this valuable chance!
Category: Juniper Exam
2015 Latest Updated JN0-360 VCE Free Download from Braindump2go
We never believe in second chances and Braindump2go brings you the best JN0-360 Exam Preparation Materials which will make you pass in the first attempt.We guarantee all questions and answers in our JN0-360 Dumps are the latest released, we check all exam dumps questions from time to time according to Juniper Official Center, in order to guarantee you can read the latest questions!
Exam Code: JN0-360
Exam Name: Juniper Networks Certified Internet Specialist SP (JNCIS-SP)
Certification Provider: Juniper
Braindump2go Shares the Latest Free Official Microsoft 70-411 Exam Training Questions and Answers(71-80)
QUESTION 71
Your network contains an Active Directory domain named contoso.com. All domain controllers run Windows Server 2012 R2. You pre-create a read-only domain controller (P.QDC) account named RODC1. You export the settings of RODC1 to a file named File1.txt. You need to promote RODC1 by using File1.txt.
Which tool should you use?
A. The Dcpromo command
B. The Install-WindowsFeature cmdlet
C. The Install-ADDSDomainController cmdlet
D. The Add-WindowsFeature cmdlet
E. The Dism command
Answer: A
Explanation:
http://technet.microsoft.com/en-us/library/jj574152.aspx
If you have experience creating read-only domain controllers, you will discover that the installation wizard has the same graphical interface as seen when using the older Active Directory Users and Computers snap-in from Windows Server 2008 and uses the same code, which includes exporting the configuration in the unattend file format used by the obsolete dcpromo."
"The Summary dialog enables you to confirm your settings. This is the last opportunity to stop the installation before the wizard creates the staged account. Click Next when you are ready to create the staged RODC computer account. Click Export Settings to save an answer file in the obsolete dcpromo unattend file format."
2014 Latest Juniper JN0-370 Exam Dump Free Download!
QUESTION 1
Node devices provide which three connectivity functions on QFabric systems? (Choose three.)
A. Connect to servers
B. Connect to Director groups
C. Connect to storage devices
D. Connect to external networks
E. Connect to redundant server Node groups
Answer: ACD
2014 Latest Juniper JN0-332 Exam Dump Free Download!
QUESTION 1
Which configuration keyword ensures that all in-progress sessions are re-evaluated upon committing a security policy change?
A. policy-rematch
B. policy-evaluate
C. rematch-policy
D. evaluate-policy
Answer: A
2014 Latest Juniper JN0-314 Exam Dump Free Download!
QUESTION 1
On a MAG Series device, where is the preauthentication sign-in message configured?
A. On the configuration page for the sign-in notification message
B. On the wireless user realm authentication policy
C. On the sign-in policy of the URL being used by the wireless users
D. On the sign-in page of the URL being used by the wireless users
Answer: C
2014 Latest Juniper JN0-311 Exam Dump Free Download!
QUESTION 1
Which two configurations are made using the QoS Setup Wizard? (Choose two.)
A. Assign applications to traffic classes.
B. Use ToS/DSCP values for traffic classes.
C. Exclude subnets from QoS management.
D. Select dedicated vs. over-subscribed circuits.
Answer: AD
2014 Latest Juniper JN0-141 Exam Dump Free Download!
QUESTION 1
Which three statements are true about Host Checker? (Choose three.)
A. Host Checker can collect information for use with MAC authentication.
B. Host Checker can modify a role assignment immediately if a policy fails.
C. Host Checker can be invoked before a user is allowed to sign in to the Infranet Controller.
D. The Host Checker Integrity Measurement Verifier (IMV) works only with Odyssey Access Client.
E. The Host Checker Integrity Measurement Collector (IMC) can run on Windows, Mac, and Linux systems.
Answer: B C E
2014 Latest Juniper JN0-130 Exam Dump Free Download!
QUESTION 1
If all OSPF routers on a broadcast network have the same OSPF priority, what parameter is used to determine the new BDR at the time of a DR failure?
A. area ID
B. router ID
C. loopback address
D. IP address of interface on broadcast network
Answer: B
2014 Latest Juniper JN0-101 Exam Dump Free Download!
QUESTION 1
What is the purpose of a network mask?
A. It is used to identify the maximum hop count of a subnetwork
B. It is used to identify an IP address as either private or public
C. It is used to identify the network to which an IP address belongs
D. It is used to identify the total number of bits present in an IP address
Answer: C
2014 Latest Juniper JN0-120 Exam Dump Free Download!
QUESTION 1
Which type of cable is required to access the router’s console port from a PC?
A. modem
B. Ethernet
C. null modem
D. straight-through
Answer: C
2014 Latest Juniper JN0-643 Exam Demo Free Download!
QUESTION 1
Which command prevents Layer 2 loops if the switch stops receiving spanning-tree keepalives on port ge-1/0/1?
A. [edit protocols rstp]
user@switch# show
interface ge-1/0/1 {
bpdu-block;
}
B. [edit protocols layer2-control]
user@switch# show
interface ge-1/0/1 {
bpdu-time-out-action {
block;
alarm;
}
}
C. [edit protocols layer2-control]
user@switch# show
bpdu-block {
interface ge-1/0/1;
}
D. [edit protocols rstp]
interface ge-1/0/1
{
no-root-port;
}
Answer: D
QUESTION 2
Click the Exhibit button.
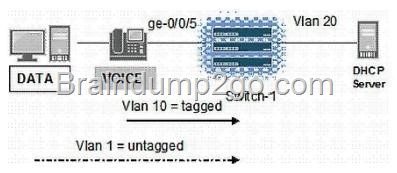
You are attaching into an EX Series switch-1a legacy IP phone that does not support LLDP-MED, but does allow configuration using DHCP, as shown in the exhibit.
Your existing network QoS policies dictate that VoIP traffic must traverse over VLAN 10.
Which two actions put VoIP traffic onto VLAN 10? (Choose two.)
A. Configure protocols cdp on switch-1.
B. Manually configure the voice VLAN on the IP phone.
C. Configure vlan 1 under forwarding-options bootp.
D. Configure interface ge-0/0/5 under forwarding-options bootp.
Answer: BD
QUESTION 3
What are three types of port designation specific to Private VLANs? (Choose three.)
A. Promiscuous ports
B. Transparent ports
C. PVLAN trunk ports
D. Designated ports
E. Isolated ports
Answer: ACE
QUESTION 4
Click the Exhibit button.
![clip_image001[4] clip_image001[4]](http://examgod.com/l2pimages/b11e64c90e8c_7880/clip_image0014_thumb.jpg)
Looking at the output in the exhibit, why is the BGP neighbor not in Established state?
A. BGP Refresh is not supported.
B. Multihop is not configured.
C. The peer address is not reachable.
D. Authentication is configured.
Answer: B
QUESTION 5
Which two statements about MVRP on EX Series switches are true? (Choose two.)
A. MVRP can add VLANs on access interfaces.
B. MVRP can add VLANs on trunk interfaces.
C. MVRP adds VLANs on MVRP-enabled interfaces by default.
D. MVRP is in transparent mode on MVRP-enabled interfaces by default.
Answer: BC
QUESTION 6
Your customer has five office locations.
Each office location has 20 VLANs configured, one for each department.
Your engineering team has recently secured a government contract with strict regulations which require that engineers be placed into separate workgroups.
These workgroups cannot communicate with each other.
Without changing the primary VLAN assignments, which JUNOS feature meets this requirement with minimal configuration?
A. Create a series of firewall filters to block users in each workgroup.
B. Configure a Private VLAN and assign each workgroup a secondary VLAN.
C. Configure Virtual Private LAN Service to isolate broadcast domain.
D. Turn off the default BUM (Broadcast, unknown, multicast) flooding mode.
Answer: B
QUESTION 7
Click the Exhibit button.
![clip_image001[6] clip_image001[6]](http://examgod.com/l2pimages/b11e64c90e8c_7880/clip_image0016_thumb.jpg)
In the exhibit, switches S1, S2, and S3 have Q-in-Q tunneling configured between Site 1 and Site 2.
Which configuration on switch S1 allows Site 1 and Site 2 to exchange Cisco Discovery Protocol (CDP), but blocks VLAN Trunking Protocol (VTP) between Site 1 and Site 2?
A. {master:0}[edit vlans provider-vlan]
user@S1# set dot1q-tunneling layer2-protocol-tunneling cdp
B. {master:0}[edit vlans provider-vlan]
user@S1# set dot1q-tunneling l2tp cdp
C. {master:0}[edit vlans provider-vlan]
user@S1# set dot1q-tunneling layer2-protocol-tunneling deny vtp
D. {master:0}[edit vlans provider-vlan]
user@S1# set dot1q-tunneling l2tp deny vtp
Answer: A
QUESTION 8
A coffee shop offering free Internet service to customers wants to implement the following security policies:
1. Every customer must agree to a set of terms and conditions before accessing the Internet.
2. Log out customers that are logged in for more than one hour.
3. Log out customers that are idle for more than 5 minutes.
4. Authenticate employee desktop computers with known hardware addresses in the office of the coffee shop to access the Internet without the above restrictions.
The following configuration has been applied to the switch:
set access radius-server 172.16.14.26 port 1812
set access radius-server 172.16.14.26 secret Am@zingC00f33
set access profile dot1x authentication-order radius
set access profile dot1x radius authentication-server 172.27.14.226
What would you add to implement these policies?
A. set protocols dot1x authenticator interface ge-0/0/12.0 supplicant multiple
set protocols dot1x authenticator interface ge-0/0/12.0 mac-radius
set protocols dot1x authenticator authentication-profile-name dot1x
set services captive-portal authentication-profile-name dot1x
set services captive-portal interface ge-0/0/12.0
set services captive-portal secure-authentication https
set services captive-portal custom-options header-message "Welcome to Our Coffee Shop"
set services captive-portal custom-options banner-message "Terms and Conditions of Use"
B. set protocols dot1x authenticator interface ge-0/0/12.0 supplicant multiple
set protocols dot1x authenticator authentication-profile-name dot1x
set services captive-portal authentication-profile-name dot1x
set services captive-portal interface ge-0/0/12.0
set services captive-portal secure-authentication https
set services captive-portal custom-options header-message "Welcome to Our Coffee Shop"
set services captive-portal custom-options banner-message "Terms and Conditions of Use"
C. set protocols dot1x authenticator interface ge-0/0/12.0 supplicant multiple
set protocols dot1x authenticator interface ge-0/0/12.0 mac-radius
set protocols dot1x authenticator authentication-profile-name dot1x
set services captive-portal authentication-profile-name dot1x
set services captive-portal interface ge-0/0/12.0
set services captive-portal interface ge-0/0/12.0 idle-timeout 300
set services captive-portal interface ge-0/0/12.0 user-timeout 3600
set services captive-portal secure-authentication https
set services captive-portal custom-options header-message "Welcome to Our Coffee Shop"
set services captive-portal custom-options banner-message "Terms and Conditions of Use"
D. set protocols dot1x authenticator interface ge-0/0/12.0 supplicant multiple
set protocols dot1x authenticator interface ge-0/0/12.0 mac-radius
set protocols dot1x authenticator interface ge-0/0/12.0 idle-timeout 300
set protocols dot1x authenticator interface ge-0/0/12.0 user-timeout 3600
set protocols dot1x authenticator authentication-profile-name dot1x
set services captive-portal authentication-profile-name dot1x
set services captive-portal interface ge-0/0/12.0
set services captive-portal secure-authentication https
set services captive-portal custom-options header-message "Welcome to Our Coffee Shop"
set services captive-portal custom-options banner-message "Terms and Conditions of Use"
Answer: A
QUESTION 9
Click the Exhibit button.
![clip_image001[8] clip_image001[8]](http://examgod.com/l2pimages/b11e64c90e8c_7880/clip_image0018_thumb.jpg)
In the PIM-SM network in the exhibit, all links in the topology have the same IGP metric configured.
Which link will not be on the RPT?
A. R1-R4
B. R3-R6
C. R4-R5
D. R5-R6
Answer: A
QUESTION 10
Click the Exhibit button.
![clip_image001[10] clip_image001[10]](http://examgod.com/l2pimages/b11e64c90e8c_7880/clip_image00110_thumb.jpg)
In the exhibit, Site 1 is sending traffic on VLANs 100, 200, and 300.
The provider operating switch S1 must configure Q-in-Q tunneling to transport VLANs 100 and 200 to Site2.
The provider must configure switch S1 to block traffic received from site 1 on VLAN 300.
Which configuration accomplishes this goal?
A. {master:0}[edit vlans pv200]
user@S1# show
vlan-id 200;
interface {
ge-0/0/0.0;
ge-0/0/1.0;
}
dot1q-tunneling {
customer-vlans [ 100 200 ];
}
B. {master:0}[edit vlans pv200]
user@S1# show
vlan-id [100 200];
interface {
ge-0/0/0.0 {
dot1q-tunneling {
block-vlans 300;
}
}
ge-0/0/1.0;
}
C. {master:0}[edit vlans pv200]
user@S1# show
vlan-id 200;
interface {
ge-0/0/0.0;
ge-0/0/1.0;
}
dot1q-tunneling {
block-vlans 300;
}
D. {master:0}[edit vlans pv200]
user@S1# show
vlan-id 200;
interface {
ge-0/0/0.0 {
dot1q-tunneling {
customer-vlans [ 100 200 ];
}
}
ge-0/0/1.0;
}
Answer: A
QUESTION 11
Click the Exhibit button.
![clip_image001[12] clip_image001[12]](http://examgod.com/l2pimages/b11e64c90e8c_7880/clip_image00112_thumb.jpg)
The four routers in the exhibit are participating in a multi-area OSPF topology.
Node B (in the upper right-hand corner) is an ASBR advertising an external route.
Node A (lower left-hand corner) receives the external route and begins to forward traffic to the ASBR.
How many hops will the packets take through this topology? (Do not count node A.)
A. 2
B. 3
C. 4
D. 5
Answer: C
QUESTION 12
Click the Exhibit button.
![clip_image001[14] clip_image001[14]](http://examgod.com/l2pimages/b11e64c90e8c_7880/clip_image00114_thumb.jpg)
The phone connected to switch-1 in the exhibit cannot communicate with the rest of the network.
How do you solve this problem?
A. Add the VLAN named voice as a member of the trunk on interface ge-0/0/12.0.
B. Configure the voice VLAN on interface ge-0/0/6.0.
C. Add interface ge-0/0/12.0 to the ethernet-switching-options voip hierarchy.
D. Configure LLDP-MED for interface ge-0/0/12.0.
Answer: A
QUESTION 13
You are AS 6573.Which AS path regular expression matches only routes originated in your AS?
A. "6573.*"
B. ".*"
C. "{"
D. "^$"
Answer: D
QUESTION 14
Which protocol reachability is advertised by OSPFv2? (Choose two.)
A. IPv4
B. IPv5
C. IPv6
D. ISO
Answer: AD
QUESTION 15
Click the Exhibit button.
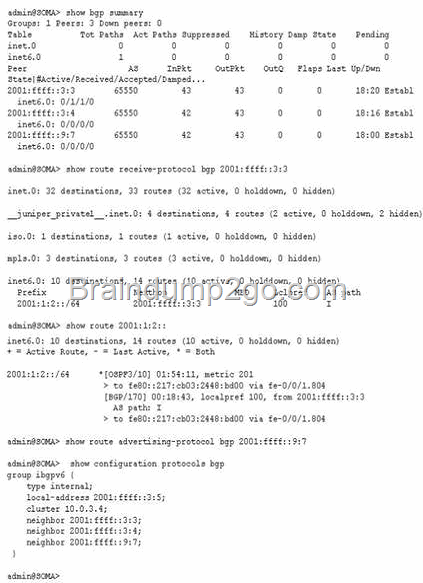
You are using an IBGP route reflector within your network.
Your route reflector has received the 2001:1:2::/64 prefix, but it is not advertising the prefix to its cluster members.
After examining the route reflector, you notice the output shown in the exhibit.
Which configuration statement causes the route reflector to transmit the route to its IBGP peers?
A. set protocols bgp group ibgpv6 advertise-inactive
B. set protocols bgp group ibgpv6 accept-remote-nexthop
C. set protocols bgp group ibgpv6 multipath
D. set protocols bgp group ibgpv6 include-mp-next-hop
Answer: A
Passing your Juniper JN0-643 Exam by using the latest Juniper JN0-643 Exam Demo Full Version: http://www.braindump2go.com/jn0-643.html